At the intersection of innovation and security,
an AI-infused CRM dashboard
Client:
Cisco
Timeline:
8 months
Year:
2023
Cisco
Timeline:
8 months
Year:
2023
My Role:
UX Design, UX Strategy
Team:
3 Designers, 2 UX Researchers, 1 Strategist
UX Design, UX Strategy
Team:
3 Designers, 2 UX Researchers, 1 Strategist
Project Overview
To design an advanced solution that harnesses artificial intelligence for providing on-the-spot training and context-specific learning experiences to employees within an organization, with the ultimate goal of providing the Chief Information Security Officer with a real-time assessment of the organization's overall health and security status.
Chief Information Security Officer (CISO): is a high-ranking executive responsible for overseeing and managing an organization's information security and cybersecurity strategy.
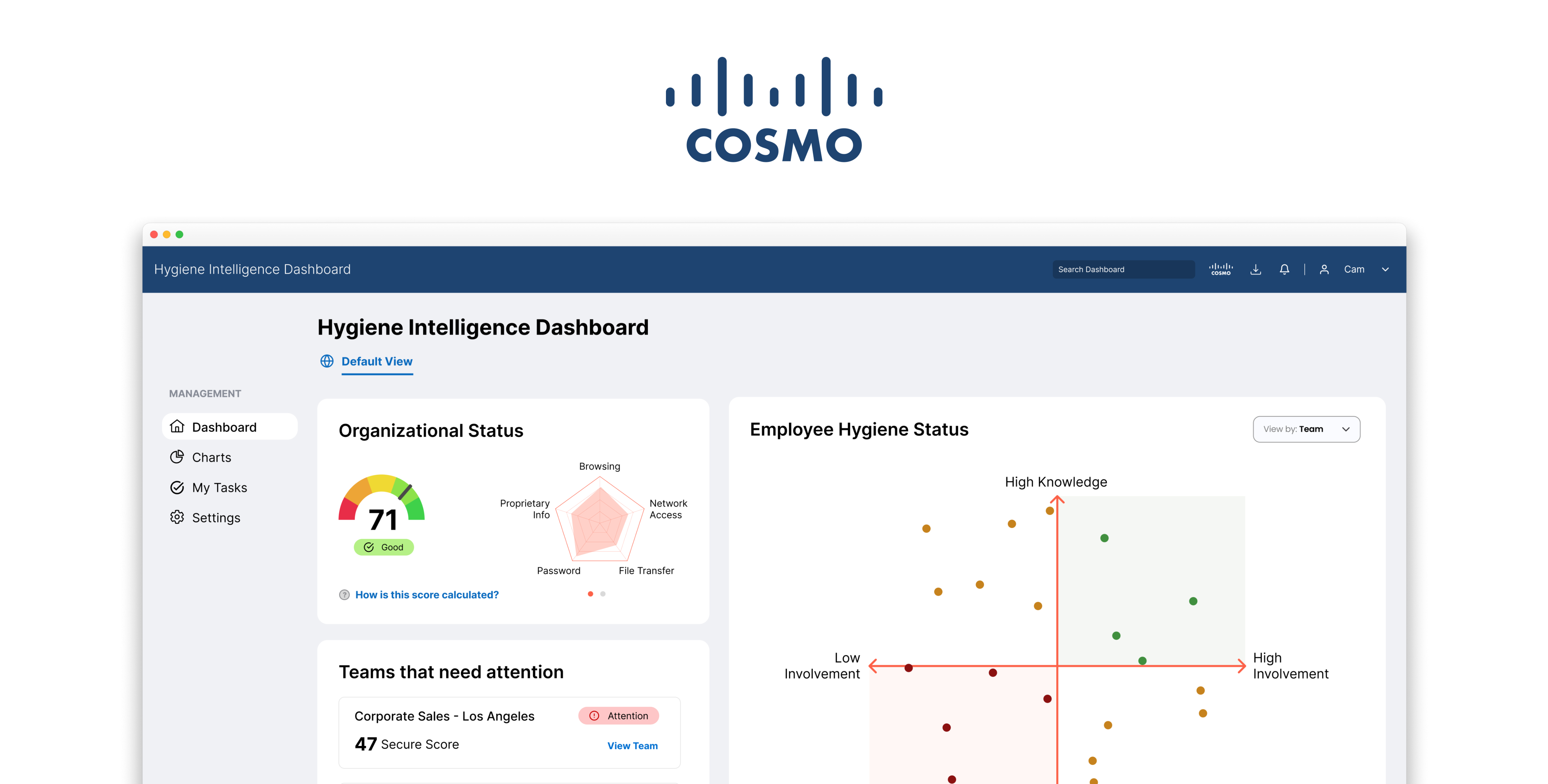
Solution
A cutting-edge dashboard that consolidates and assesses data collected by the latest offering from Cisco, known as Cosmo. This product delivers a comprehensive cyber security score, equipping Chief Information Security Officers (CISOs) with invaluable insights into their organization's cybersecurity status. With this powerful metric, CISOs can effectively present compelling evidence to their higher-ups, supporting their case for enhanced cybersecurity solutions within the company.
Results
- I developed a framework enabling Cisco to collaborate with employees to foster a secure, transparent, and mutually beneficial environment by prioritizing cybersecurity and bringing it to the forefront of the organization.
-
I identified key pain points for CISOs and designed an AI/ML-driven tool that helps them create and endorse products aligned with organizational cybersecurity objectives and employee insights.
How Might We Statement?
In this fast-changing landscape of cybersecurity
How might Cisco innovate to empower security workers 5 to 10 years into the future?
Why design for CISOs?
Designing solutions tailored for CISOs is essential, as CISOs play a pivotal role in shaping the overall health of an organization's security posture. They are entrusted with the critical responsibility of safeguarding sensitive data, ensuring regulatory compliance, and implementing robust security strategies, making them the key to fortifying an organization's defenses against evolving cyber threats.
Why a crm dashboard?
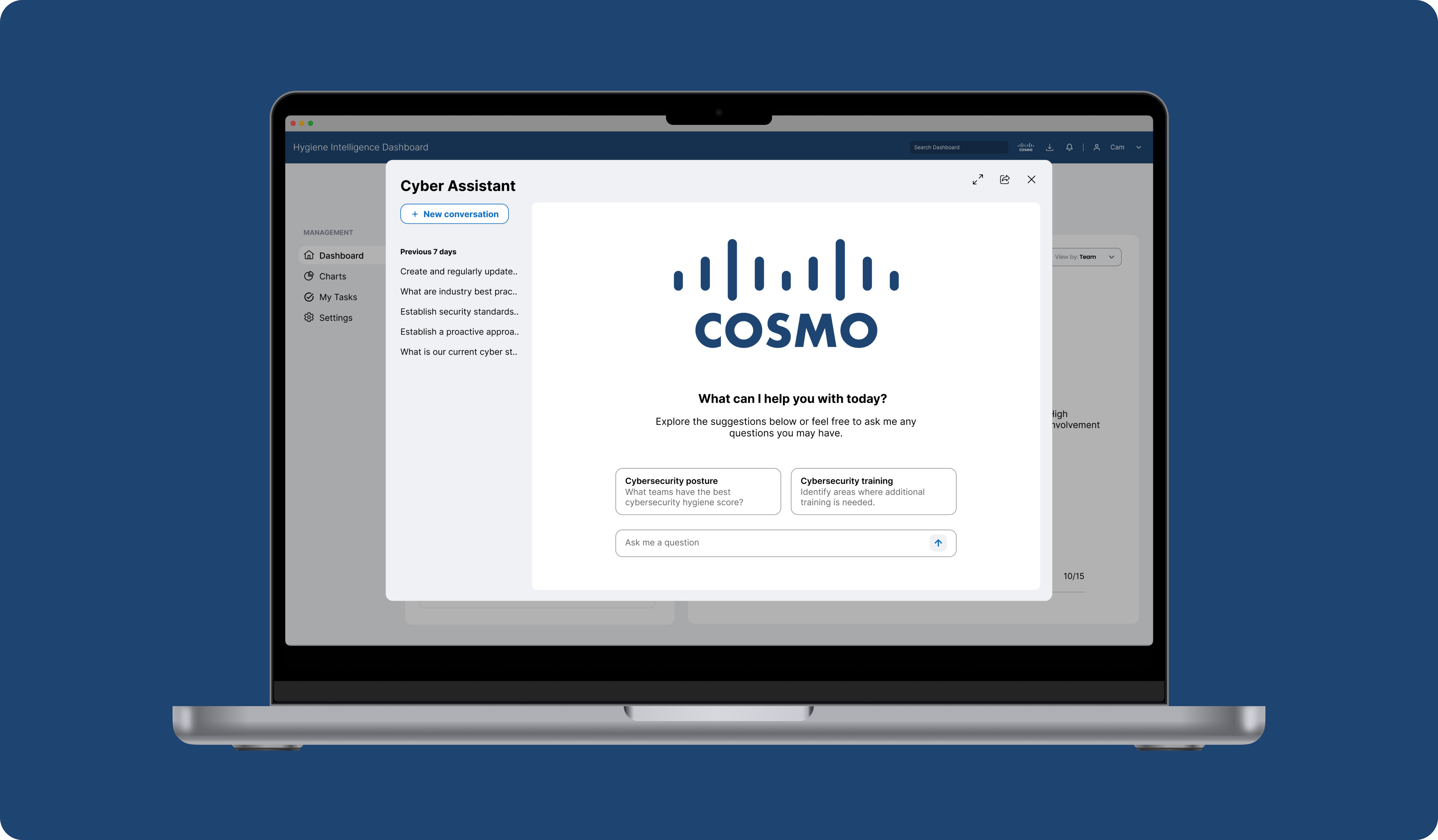
I had the opportunity to design and reimagine cybersecurity training by introducing an AI companion that collects and synthesizes employee data, like users' habits while on the internet. Cosmo is also designed to aid employees in navigating company computers, offering context-aware learning and proactive suggestions to enhance decision-making during internet use.
A well-designed CRM Dashboard synthesizes the collected data and becomes a tool for CISOs to monitor cybersecurity practices, track training progress, and effectively evaluate security scores across their workforce. This allows them to take proactive measures to enhance the organization's security posture, mitigating risks and ensuring data protection in an increasingly complex threat landscape.
Introducing Cosmo
The following illustrates how Cosmo could assist Cisco employees, drawing from a real-life scenario where hackers masquerade as government agencies to steal confidential information.
In this scenario, a company employee filing their taxes for the first time looks to YouTube to walk them through the steps of doing their taxes. They don’t realize that the link provided isn’t the actual link to the IRS website. It's a fake website used to steal their IRS login credentials.
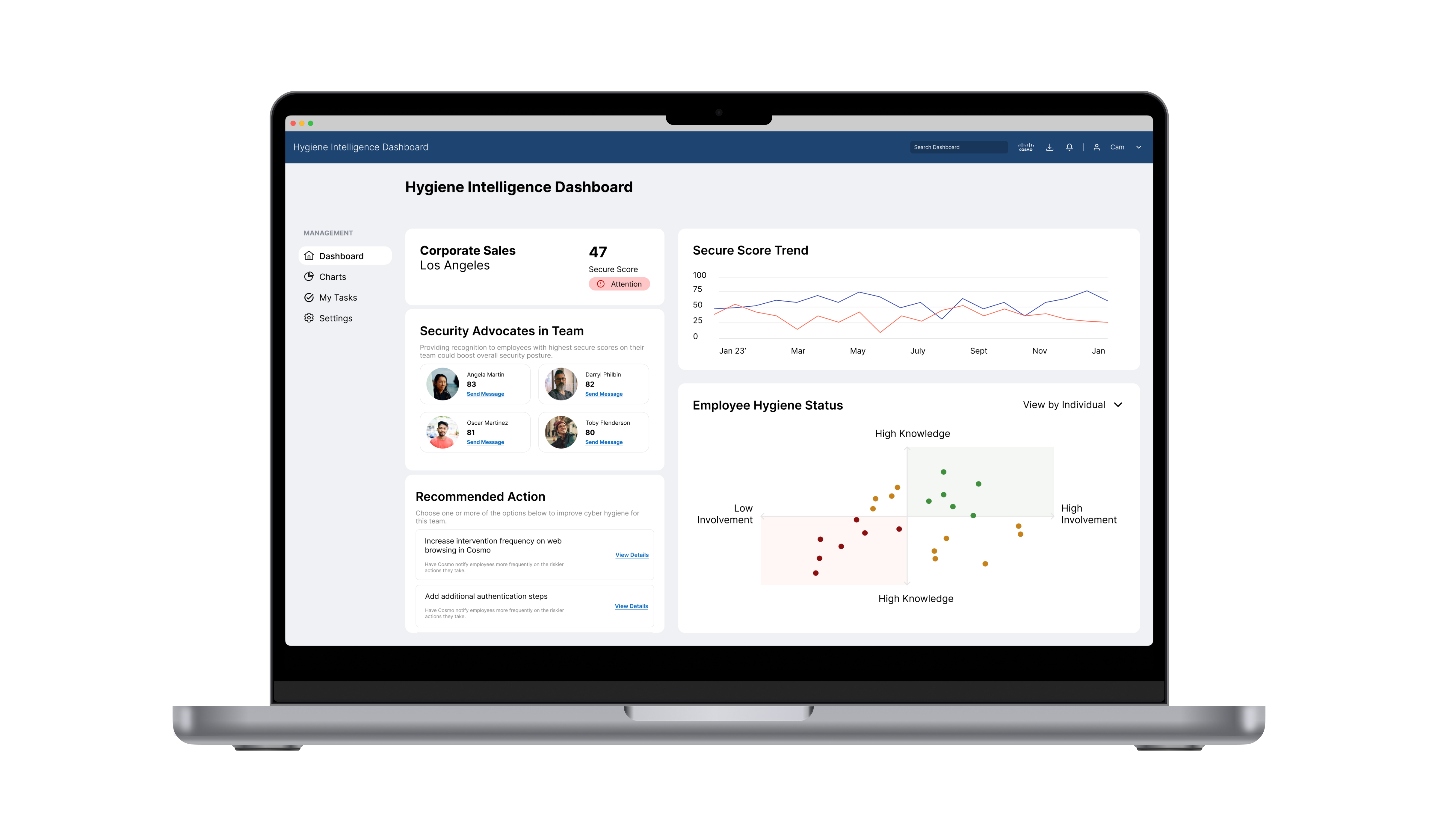
Key Dashboard Features
In-depth cybersecurity hygiene score
Through the constant monitoring that Cosmo does, CISOs can assess the effectiveness of their security measures, as it provides a comprehensive score out of 100. This valuable score offers a quick, easily understandable overview of the organization's security readiness. With this feature, CISOs can proactively identify areas that require attention, measure the impact of security initiatives, and make informed decisions to bolster the company's defense against cyber threats.
The secure score is calculated by analyzing various aspects of an employee's online cybersecurity habits. We consider factors such as the strength and uniqueness of passwords, the regularity of software updates, and employees' adherence to best online privacy practices.

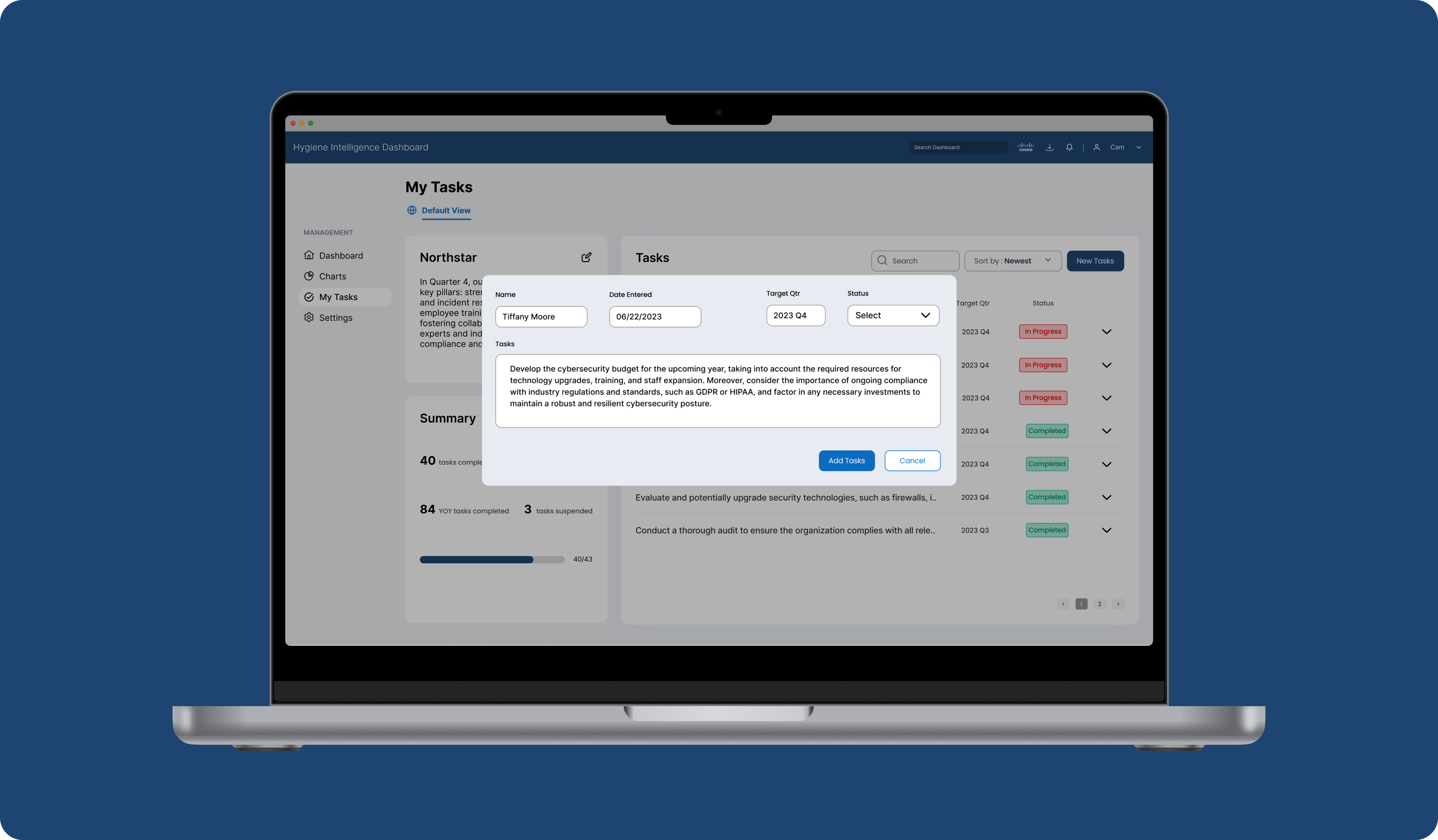
Keep track of essential OKRs and organizational strategies
A centralized hub for CISOs to track their Objectives, Key Results (OKRs), and critical security strategies. With this feature, CISOs can seamlessly set, monitor, and refine their OKRs, ensuring alignment with organizational goals. They can also map out key strategies, making overseeing their implementation and success easy. This integrated approach enhances an organization's security posture and streamlines the CISO's workflow, providing a comprehensive view of their priorities and progress within the familiar CRM interface.
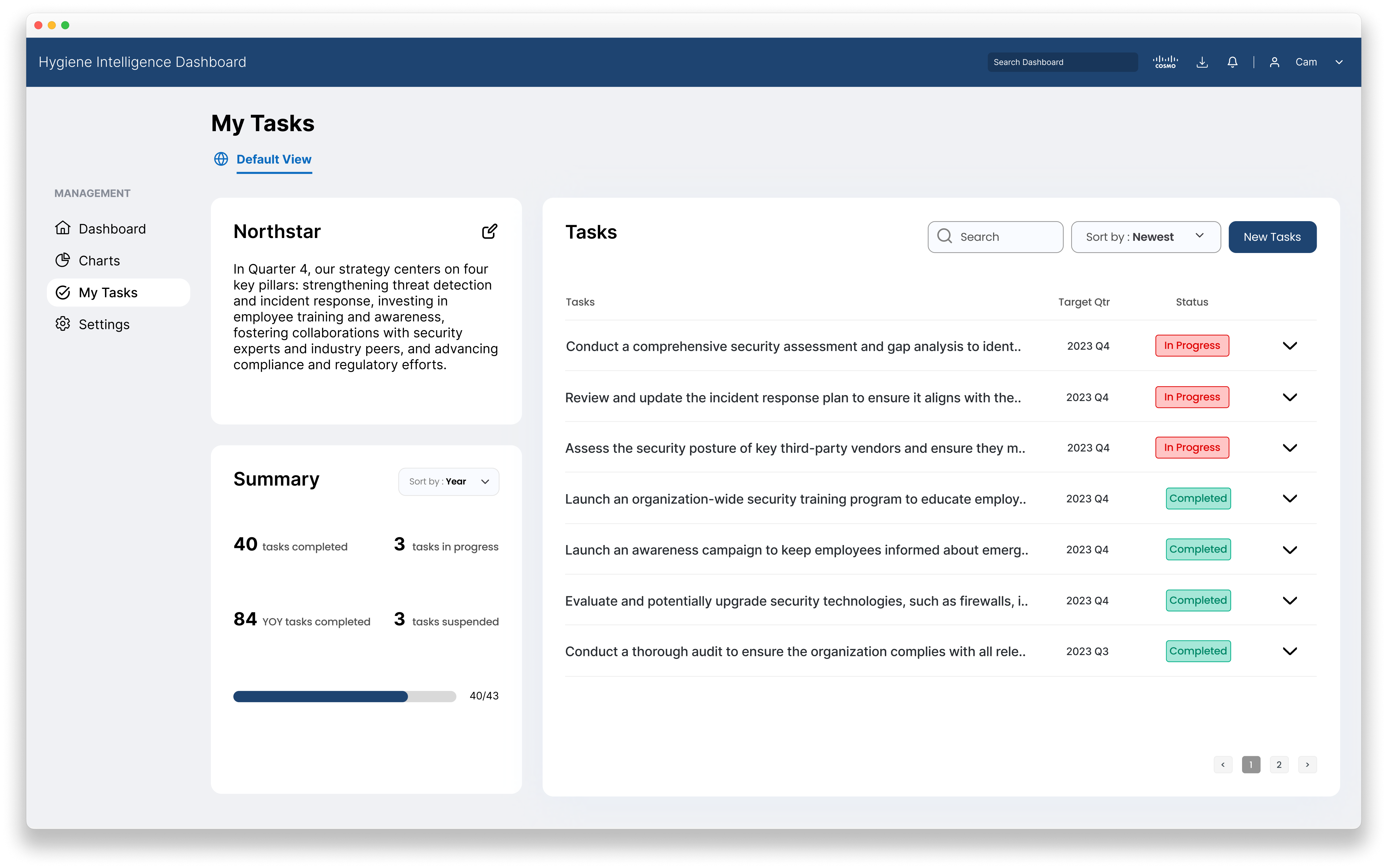
Use AI to generate detailed reports based on company cybersecurity data
This feature harnesses the power of artificial intelligence to provide Chief Information Security Officers (CISOs) with a detailed and data-driven cybersecurity report based on employees' cyber habits. This innovative technology not only monitors but also analyzes the behavior of employees within the digital environment. Collecting and processing vast amounts of data offers insights into potential security risks and compliance issues. These reports can then be used as evidence to support CISO's security strategy for their organization.
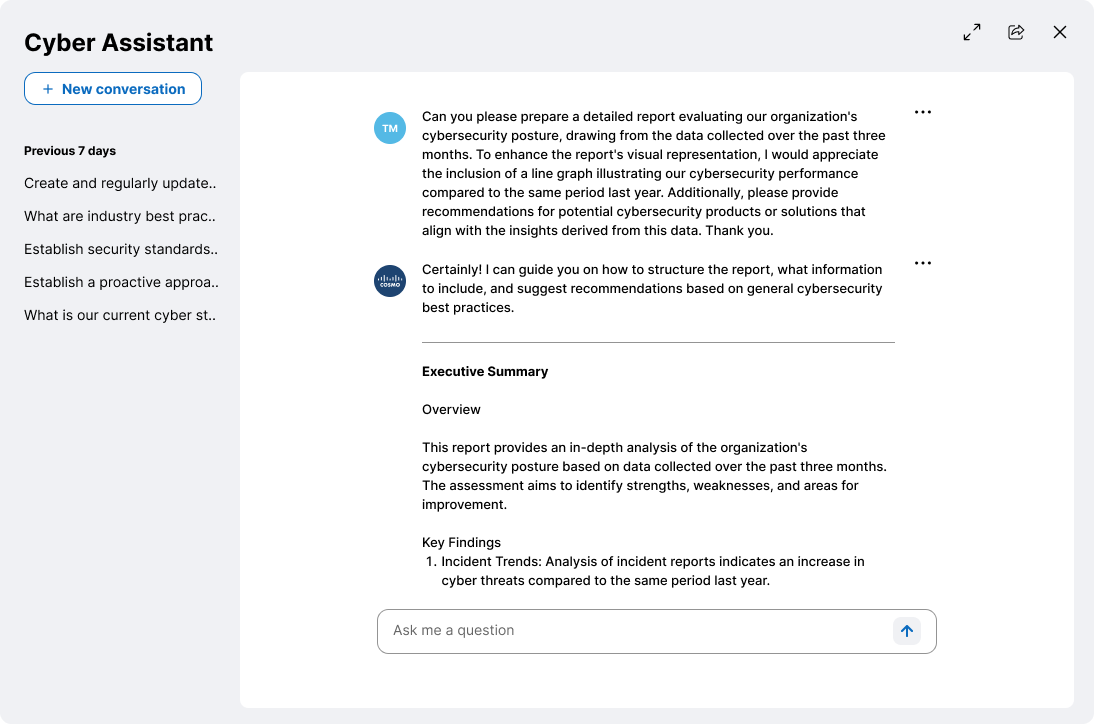
Final Designs


Lead With Research
Secondary Research
When I began the project, my background in cyber security was limited. To compensate for this, I chose to engage in secondary research. I aimed to gain insights into Cisco's business model and the contemporary cybersecurity environment. To achieve this, I delved into extensive literature reviews, encompassing industry reports, white papers, and conference presentations.
Primary Research
Following my secondary research, I conducted interviews with internal and external stakeholders, employing semi-structured research techniques. This approach enabled me to gather diverse viewpoints regarding the content and design of the dashboard we were developing. Among those I had the privilege to interview was Mary Ann Blair, an accomplished professional who serves as the Assistant Vice President and Chief Information Security Officer (CISO) of Carnegie Mellon University. Notably, she was recognized as CISO of the Year in the education/nonprofit category by the Pittsburgh Technology Council. This provided great insights into the mindset of CISOs and what information they needed to do their jobs more efficiently.
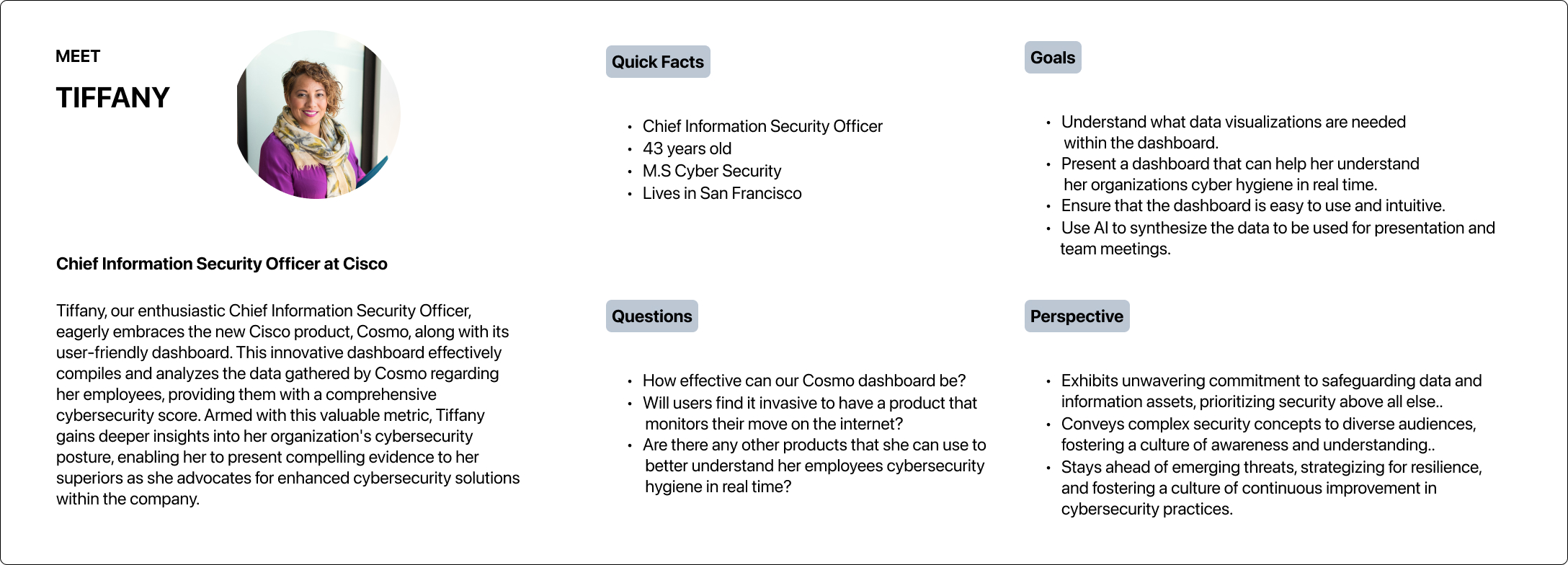
Understanding our user
My primary and secondary research enabled me to create a well-defined persona as a constant reference point, ensuring that the CISO's preferences and needs remained central to the dashboard's design process.
Site Visit
After personally conducting 30+ semi-structured interviews with security professionals, I sat in on a design sprint led by Sarah Marshall, Director of Design Operations, at the Cisco headquarters in San Francisco.
This visit helped me better understand what CISOs expect regarding a comprehensive dashboard and what it’s like to participate in a sprint with a cross-functional team.

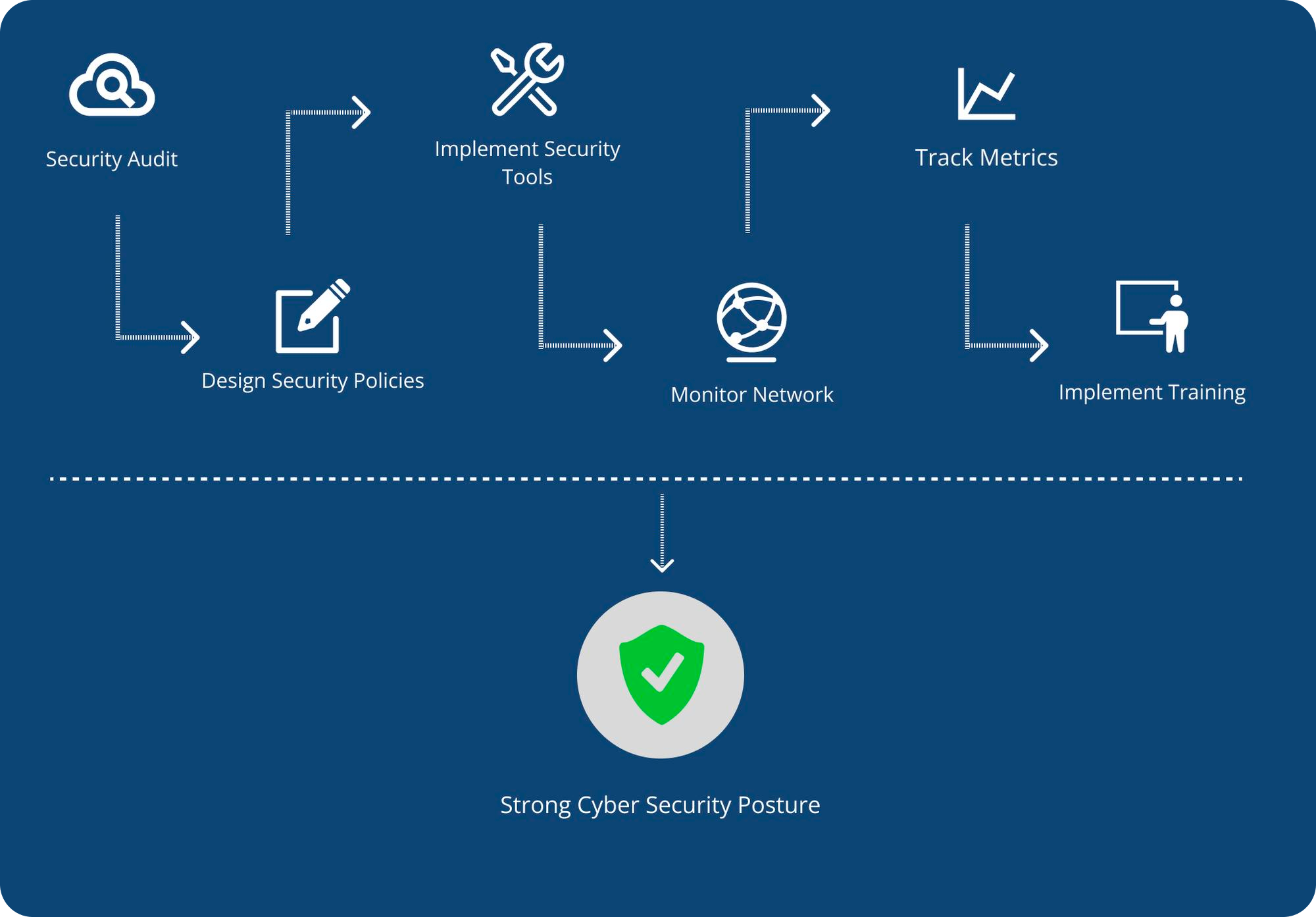
Cybersecurity Conceptual Model
Following my research, I opted to develop a conceptual framework outlining how a Chief Information Security Officer (CISO) can establish an environment fostering a robust cybersecurity posture within an organization. This endeavor granted me an overarching perspective on the adaptable mindset a CISO should adopt, tailored to the organization's level of maturity. This understanding significantly informed my ultimate design, wherein I prioritized including essential components such as the capacity to conduct security audits at any given moment and seamless implementation of training as required.
Affinity Mapping
We collaborated on synthesizing and affinity mapping to extract valuable insights from our research. This collaborative approach was particularly beneficial as it allowed us to combine our expertise and perspectives, resulting in a more comprehensive analysis of our research data. By synthesizing and affinity mapping, we could identify patterns and connections that may have been overlooked when working individually. This collective effort enriched our understanding and enabled us to uncover deeper insights that significantly impacted our research outcomes.

Key Insights
From our research, we gathered three key insights:
01
CISOs have to advocate for design strategies and products
Chief Information Security Officers (CISOs) bear many responsibilities, including assembling evidence to justify their organization's adoption of new technology. This procedure can be quite time-intensive.
02
Observability is key to making leadership decisions quicker
The ability of a Chief Information Security Officer (CISO) to swiftly and effectively communicate and distill information about their organization's health is of utmost significance. Delays in this process can potentially result in data breaches.
03
Most CISOs don’t know the health of their organization until it’s too late
Security operates quietly in the background, making it challenging to assess the strength of your organizational security posture until a breach occurs. Unfortunately, it's already too late when a breach happens.
Prototyping
Low Fidelity / Wireframes
My design process commenced with the development of low-fidelity screens, a deliberate step taken to fine-tune the user flow. Throughout this iterative process, I consistently referred back to the conceptual model I had constructed. This model served as the guiding blueprint for integrating essential information that would empower CISOs to formulate and implement a potent cybersecurity strategy. It was a pivotal reference point, ensuring that every design element was aligned with the overarching goal of enhancing cybersecurity effectiveness.
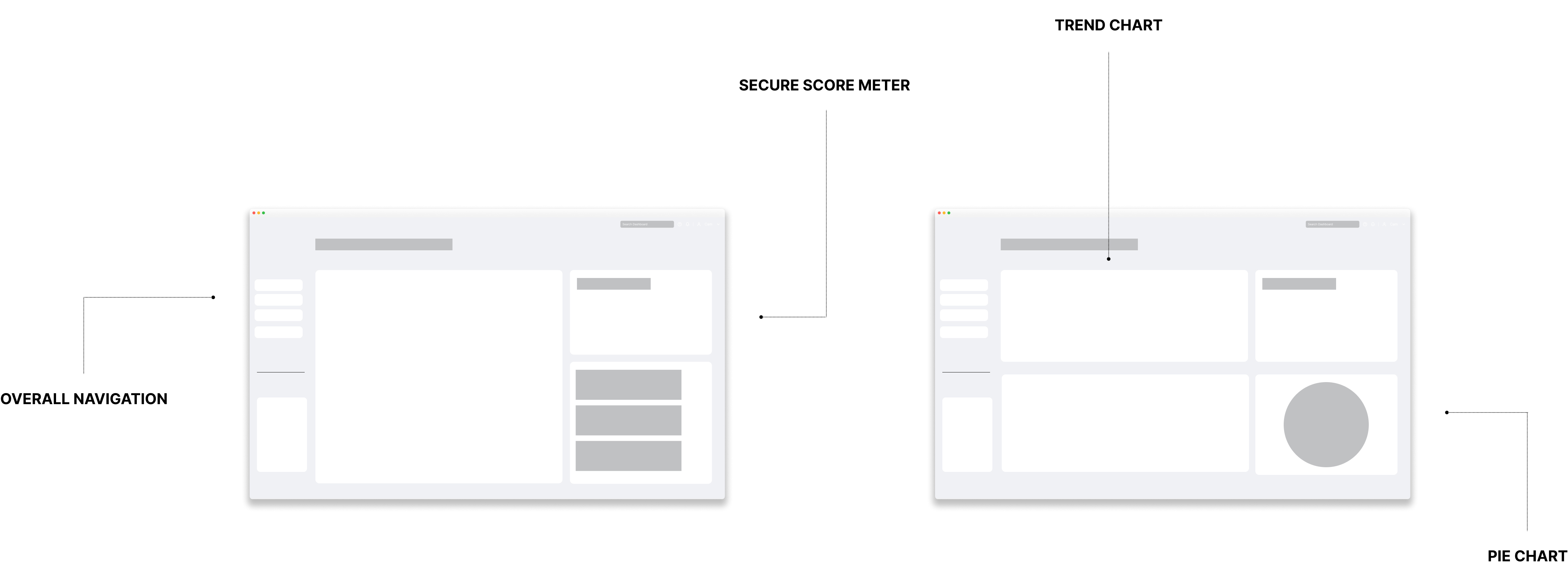

Design Iterations
Following the initial low-fidelity wireframe stage, I transitioned to mid-fidelity designs, a phase where color palettes were intentionally omitted. This strategic choice allowed me to gather valuable input from internal and external stakeholders, promoting an unbiased assessment of the design's core elements and structure. Subsequently, the feedback collected during this stage played a pivotal role in refining the final design, ensuring that it not only met but exceeded the expectations and requirements of all involved parties.


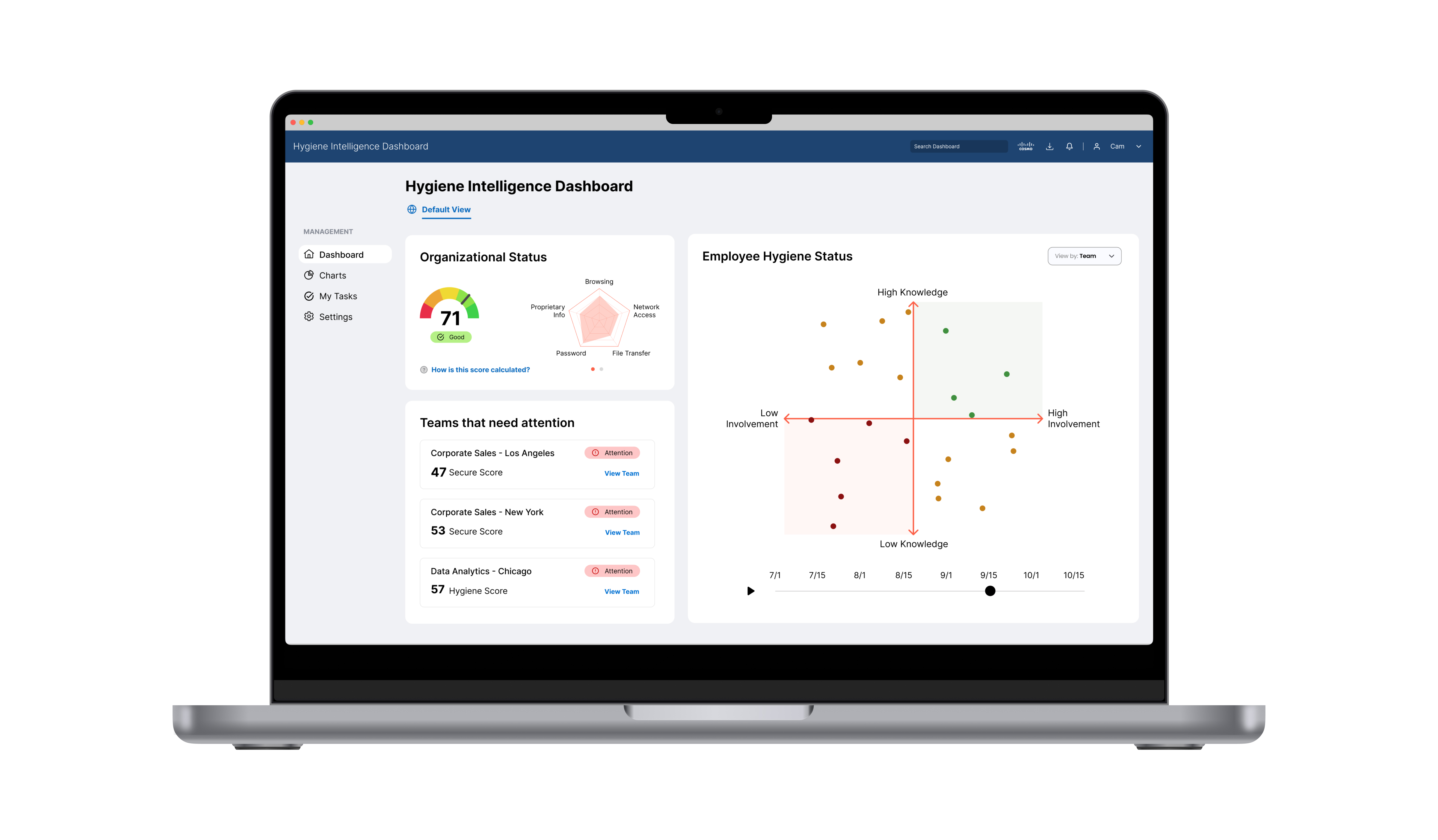
Final Design Flows
Home Screen
I crafted the dashboard with the primary goal of delivering vital information immediately upon opening. This includes displaying the organization's overall security score prominently, enhancing the user experience with interactive micro-interactions within a comprehensive map, and providing essential insights into teams requiring special attention.
Conclusion
In summary, this project was a profoundly challenging yet immensely gratifying endeavor. Initially, venturing into the cybersecurity domain without prior experience was a formidable task, propelling me into thorough research to unearth critical insights that significantly shaped the project's direction. Embracing the "messy" aspect of design was a source of genuine pleasure, as it's in those creative complexities where true innovation thrives.
Moreover, this project underscored the importance of collaboration with cross-functional teams. It underscored the significance of involving all stakeholders early in the design process to preempt the need for extensive redesign work. While moments of frustration arose, they ultimately contributed to our collective growth and the project's overall success.
I maintained a steadfast commitment to grounding design decisions in data and articulating how they would yield maximum impact. Given more time, I would have eagerly delved deeper into collaborative work with engineers and conducted usability testing with CISOs to glean their valuable feedback, further enriching the project's quality and relevance.